Resources
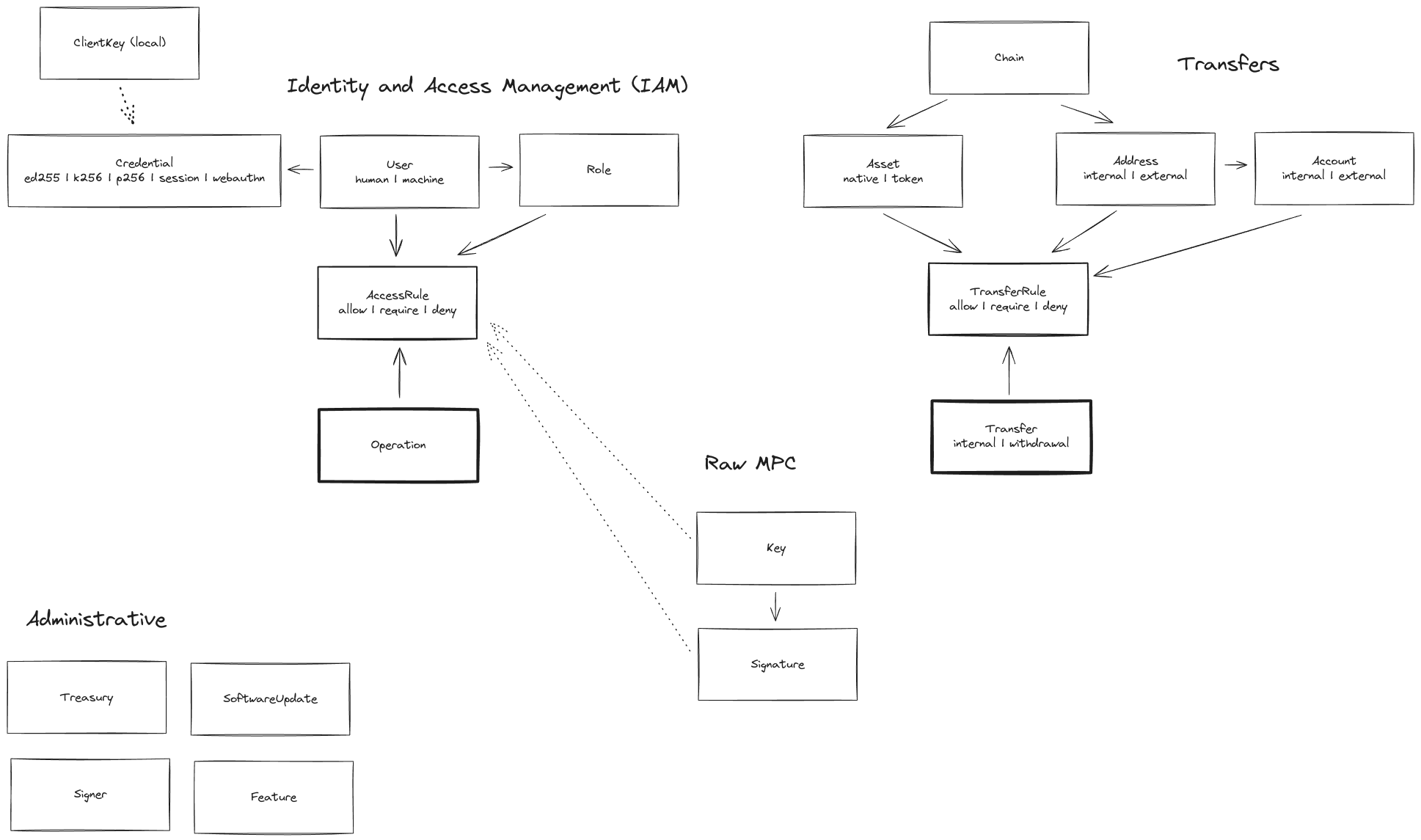
Identity and Access Management (IAM)
Useris the fundamental resource. They can behumanormachine. Each request to Treasury must be signed with aCredential, which comes in multiple variants:k256is suitable for programmatic or CLI requests,webauthn(and the time-limitedsession) is used for UI request.Rolecan be attached to users. One user may have multiple roles.AccessRules consitute the Access Policy, determining whichOperations may be initiated, approved or canceled by which users or roles
Note that an Operation cannot be directly created. Instead, each user request for a CRUD operation (if valid according the the access policy)
creates an Operation.
If an operation is authorizing, it requires approving requests; ultimately an operation will have succeeded or failed.
In the successful case, the originally requested operation (CRUD on some other resource) will be executed.
Transfers
Chainis the parent resource of bothAddress, which isinternal(if Treasury controls the key) orexternal, andAsset, which is thenative(gas) asset or a contract-basedtokenasset.Accountis an optional grouping mechanism for addresses (each address can be in at most one account)TransferRules constitute the Transfer Policy, determining which from-to routes are allowed for which assetsTransferthen is the core resource of Treasury, a semantic representation of sending an amount of an asset from one address to another.
Administrative
Treasuryis a singleton resource, with information such as its ID and current software version.Signercorresponds to the off-chain worker process creating keys and signatures using MPC protocols.SoftwareUpdateis a request to update the Treasury software at a given block (executed by the distributedsupervisorprocesses)Featureare opt-in features of the Treasury.
Raw MPC
Whereas Address and Transfer are also based on keys and signatures (with a dedicated transfer policy),
as an escape hatch users may still create
Keys for any supported curve, and correspondingSignatures in any supported format
Crucially, the access policy still applies to "Raw MPC", allowing for instance
- require access rules on the chosen key threshold, or
- required machine processes approving signature payloads