Deploy on GCP
Treasury can easily be deployed within your GCP cloud. It will be co-hosted with Cordial Systems, meaning Cordial Systems will deploy a node in their infrastracture to help secure your node via MPC and distributed policy enforcement (e.g. 2/2 or 3/4 threshold arrangement).
Deploy a VM using Treasury image
Deploy a VM using the latest Cordial Treasury image.
- Project: cordialsys
- Image: cordialsys-treasury-amd64-20251001
Soon you will be able to use the GCP marketplace to launch this more easily.
Use a VM with at least:
- 2 CPU
- 4-8 GB RAM
- 100 GB disk
If you expect very heavy usage, you should increase the machine specs. This can be done later as needed.
For the purposes of this guide, name your VM cordial-treasury.
Access Panel UI
Next we need to be able to access the "Panel UI" of Treasury to proceed with the setup.
Setup firewall rule
Create a firewall rule to allow GCP to internally forward traffic from their IAM proxy. This does not permit any external traffic.
- Name:
allow-internal-forwarding - Target tags:
treasury - Source IPv4 range:
35.235.240.0/20 - TCP Ports:
7666
Now edit your cordial-treasury VM and add the treasury network tag, so that the new firewall rule will apply.
Port forward
Now run this command, which uses the gcloud CLI, to securely connect to the Treasury Panel UI.
gcloud compute start-iap-tunnel cordial-treasury 7666 --local-host-port=localhost:7666 --project=YOUR_PROJECT
Note that your user will need to have permission to port forward, which you can get from the roles/iap.tunnelResourceAccessor role.
You can then launch the UI by visiting http://127.0.0.1:7666.
Activation
Using the Panel UI, you can now activate your Treasury instance. This securely pairs it with the Treasury node(s) running in Cordial Systems infrastructure.
To proceed, you need to provide an activation key, which you need to get from Cordial Systems.
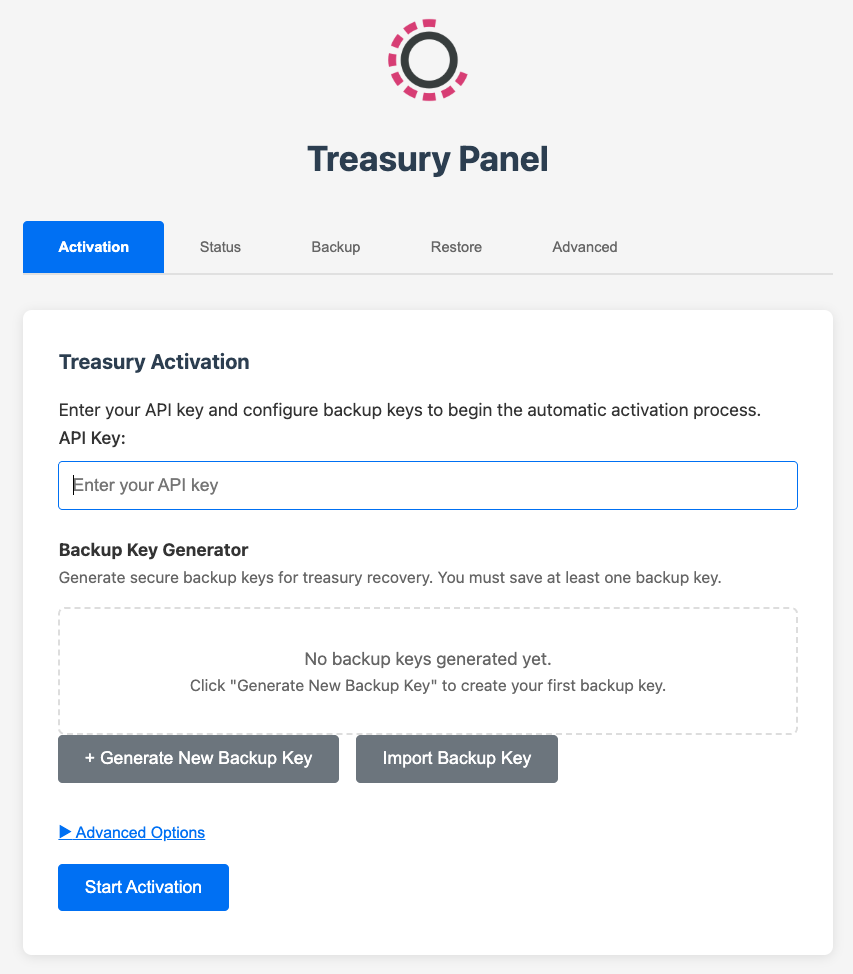
As part of activation, you'll also setup your backup encryption keys, as well as configure initial "root" or "co-root" users.